AI Security
Locktera enhances security in a RAG application by ensuring that the AI model can only use information that the user has permission to access.
Insecure Workflow
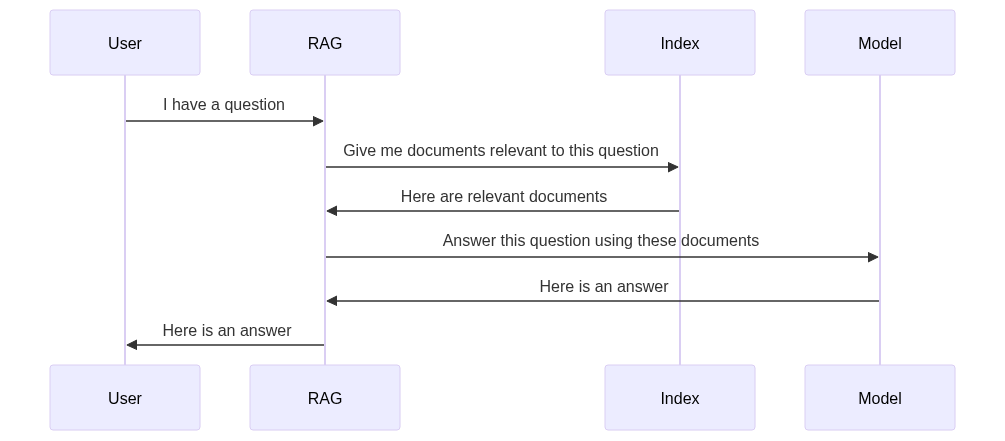
Concerns
-
Since the index has full access to all documents, if it were compromised an attacker would gain access to any sensitive information in the system.
-
If the user asks a question relevant to sensitive documents, that information will be used to inform the model and generate a response possibly containing sensitive information.
-
There is no visibility if either of the above happen - sensitive information may be stolen or utilized incorrectly, and there is no record of it occurring.
Secured Workflow
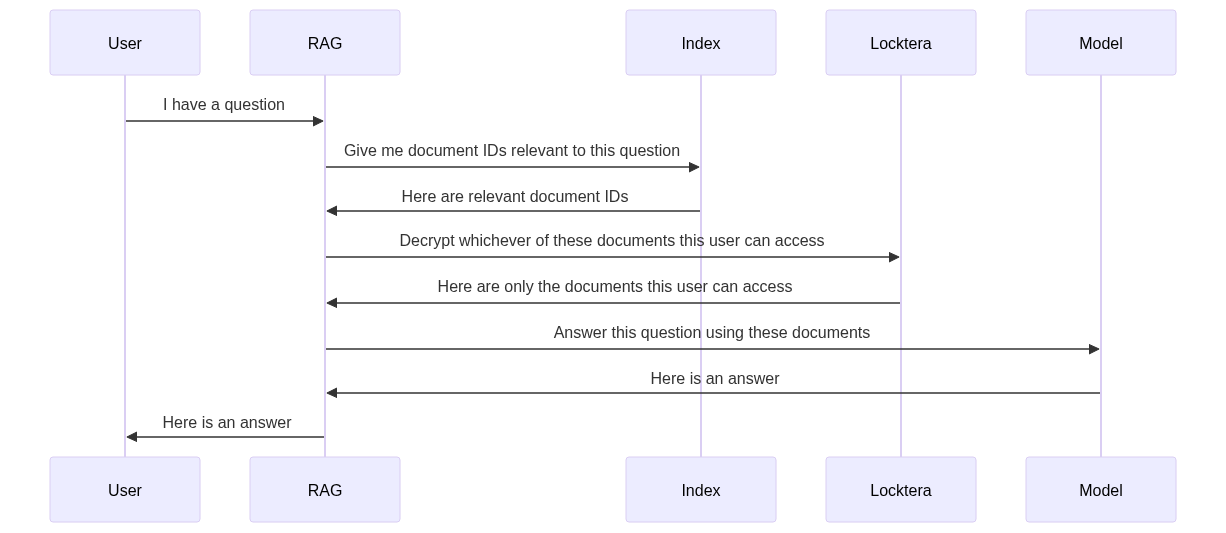
Improvements
-
Only the document IDs are stored in the index, so if it is compromised, no sensitive information is leaked.
-
Individual documents are encrypted in secure Locktera containers and can only be decrypted by users who are authorized to view them. If a user asks a question related to restricted information, Locktera would refuse to decrypt the documents, ensuring the information is not leaked.
-
Decrypting each document creates a forensic record in Locktera’s log that the document was accessed by the RAG system on behalf of the user. The full access history of any document or user can be retrieved, reviewed, and audited.
Implementation
-
During document ingestion, use the Locktera API to encode each document into a container, keeping track of its container ID.
-
During RAG indexing, map each search vector to the matching document’s container ID.
-
Use the Locktera API to manage the DRM for each container to control which users have access to which documents.
-
After determining which documents are relevant, use the Locktera API to decode the relevant documents. The API will return an error when trying to decrypt any document the user is forbidden from accessing, so simply exclude those documents from the query context.