Google Cloud Storage
Locktera Share + Google Cloud Storage Integration Guide
Locktera Share supports S3-compatible storage, allowing customers to connect their own Google Cloud Storage (GCS)buckets using a signed interoperability layer.
Step 1: Enable Interoperability and Create HMAC Keys in GCP
-
Log into the Google Cloud Console
https://console.cloud.google.com/ -
Enable Interoperability Access:
-
Navigate to Cloud Storage > Settings.
-
Go to the Interoperability tab.
-
Click Enable Interoperability Access if not already enabled.
-
-
Create HMAC Access Keys:
-
Under the same Interoperability tab, click “Create a key for a service account” or select a user account.
-
This generates an Access Key and Secret—make sure to download or copy both securely.
-
Step 2: Create or Configure a Cloud Storage Bucket
-
Go to Storage > Browser in the GCP Console.
-
Click "Create bucket" or use an existing one:
-
Enter a unique name for your bucket.
-
Choose a location (region).
-
Set access control to either fine-grained or uniform depending on your needs.
-
-
Configure permissions:
-
Under Permissions, grant read/write access to the service account or user associated with your HMAC key.
-
Recommended IAM Role:
Storage Object Adminor create a custom role with:-
storage.objects.get -
storage.objects.list -
storage.objects.create
-
-
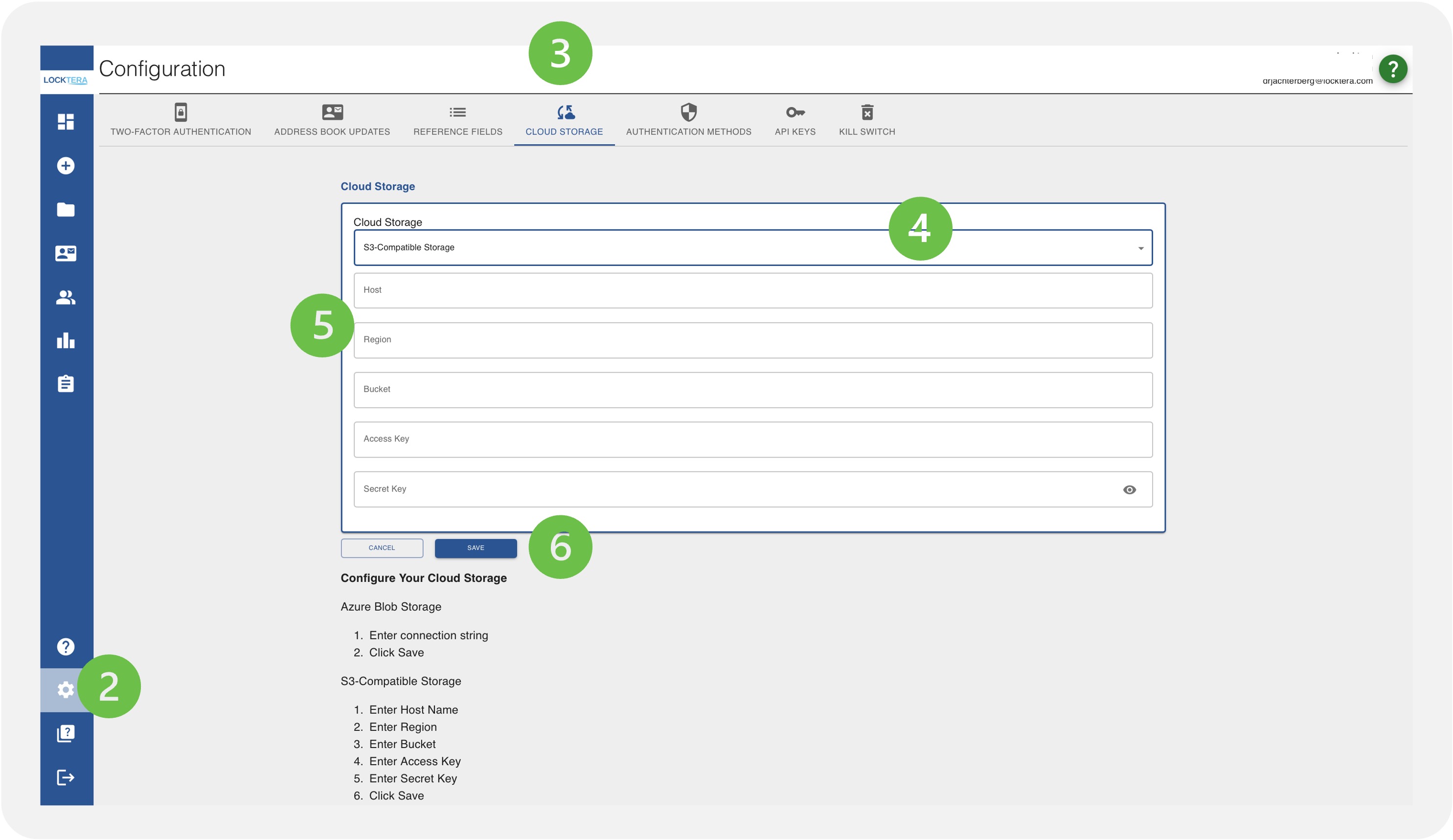
Step 3: Configure Locktera Share
In the Locktera Share interface:
-
Log into your Locktera Share System Admin Portal.
-
Navigate to settings.
-
Click Cloud Storage
-
Choose “S3-Compatible Storage” from the dropdown.
-
Enter the following details:
-
Host Name:
storage.googleapis.com -
Region:
auto(or the bucket region, e.g.,us-central1) -
Bucket: Your GCS bucket name
-
Access Key: Your HMAC Access Key
-
Secret Key: Your HMAC Secret
-
-
Click Save.
Locktera Share will now securely store files in your own GCP bucket, using signed requests that are fully compatible with Locktera’s file-level encryption and access control layers.
For enhanced security:
-
Use dedicated service accounts.
-
Rotate HMAC keys regularly.
-
Enable logging and object versioning for auditability and recovery.